TheHarvester
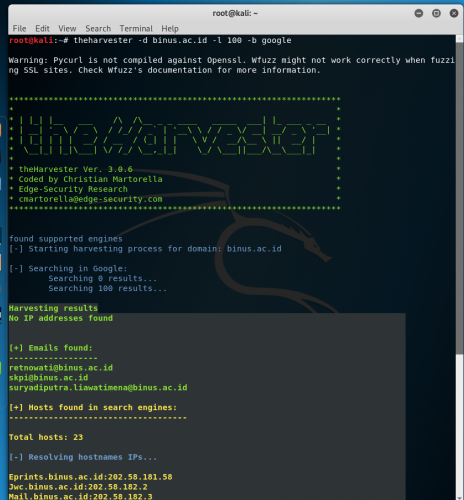
What is TheHarvester? TheHarvester is a tool for gathering e-mail accounts, subdomain names, virtual hosts, open ports/ banners, and employee names from different public sources such as google,twitter,bing,linkedin,etc. How does […]

What is TheHarvester? TheHarvester is a tool for gathering e-mail accounts, subdomain names, virtual hosts, open ports/ banners, and employee names from different public sources such as google,twitter,bing,linkedin,etc. How does […]
What is the DHCP Protocol ? The DHCP protocol or Dynamic Host Configuration Protocol is a network management protocol used on UDP/IP networks where a DHCP server dynamically assigns an IP address and other network configuration parameters […]
What is SET ? SET or social engineering toolkit, is an open-source penetration testing framework designed for social engineering and to perform advanced attacks against the human element. How does it […]
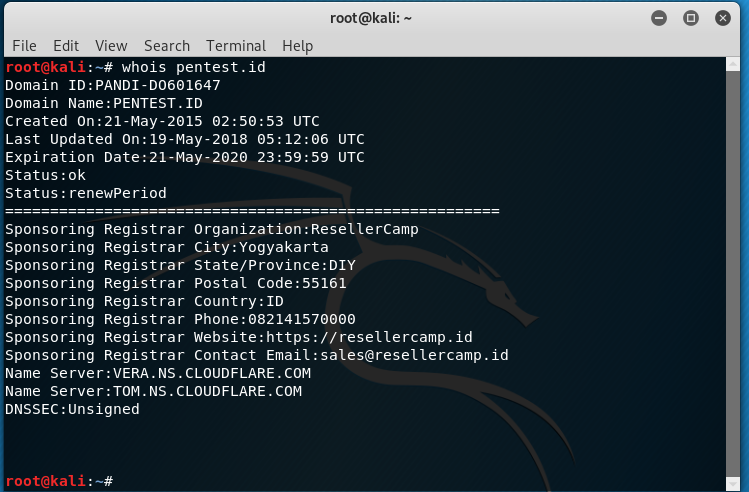
What is Whois ? The whois command searches for an object in a WHOIS database. How does it Work ? WHOIS is a query and response protocol that is widely used for […]
What is Nmap ? Nmap, short for Network Mapper, is a free, open-source tool for vulnerability scanning and network discovery. How does it work ? Nmap sends raw ip packets to […]
First, we must create a NATNetwork by going to file’s preferences. Next, set both your kali and the vulnerable vm to use NATNetwork instead of NAT. Next, check […]
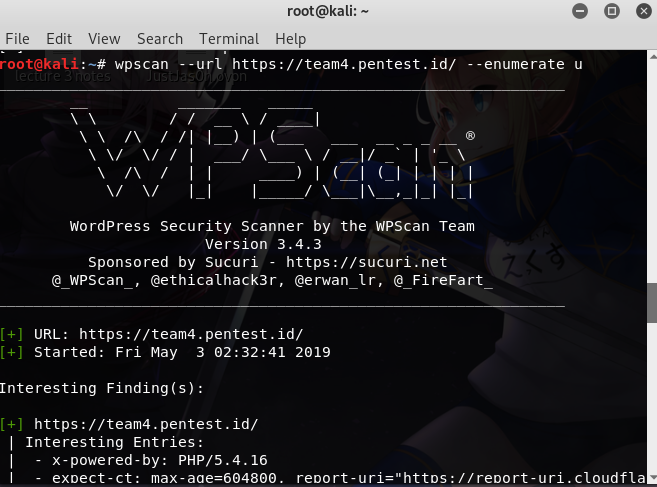
What is WPScan ? WPScan is a WordPress vulnerability scanner that can be used to scan remote WordPress installations to find security issues.It can also be used for enumeration. When […]
Link to my group’s ethical hacking final project test plan. Link: https://docs.google.com/spreadsheets/d/1darEuDthpTjAS0wZs48qC51BdKdep1KoPOgp5L0OAyM/edit?usp=sharing/
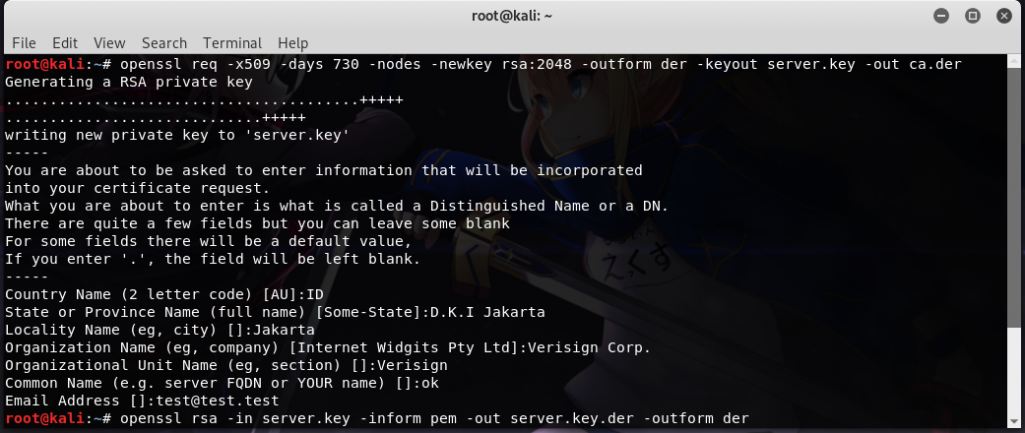
1.Set up your custom CA Certificate using OpenSSL 2.Import the generated CA certificate into the BurpSuite Proxy using the DER format This is what you will get […]
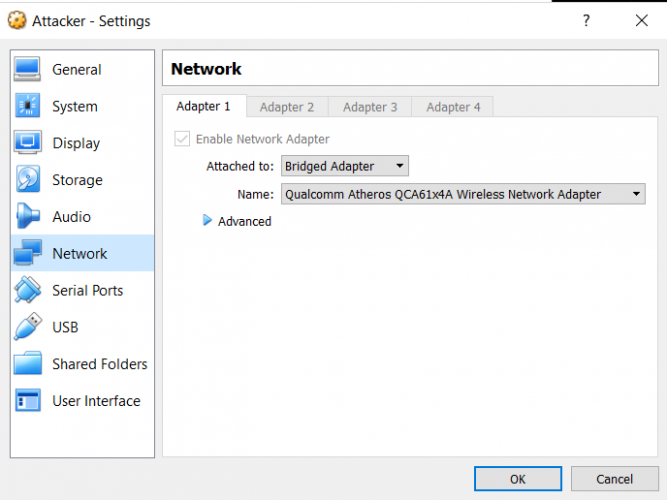
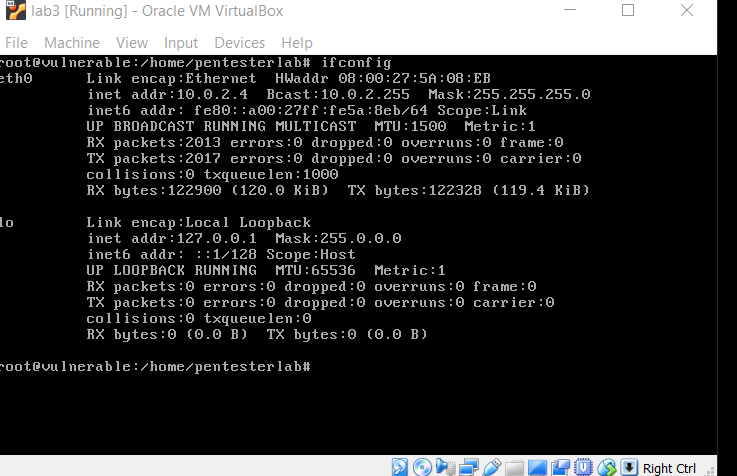
Change both machine’s network settings from “Attached to: NAT” to “Attached to: Bridged Adapter” Next, Get the victim machine’s IP address by running the ifconfig command on the command line […]