Ethical Hacking Lab 3
First, we must create a NATNetwork by going to file’s preferences. Next, set both your kali and the vulnerable vm to use NATNetwork instead of NAT. Next, check […]
First, we must create a NATNetwork by going to file’s preferences. Next, set both your kali and the vulnerable vm to use NATNetwork instead of NAT. Next, check […]
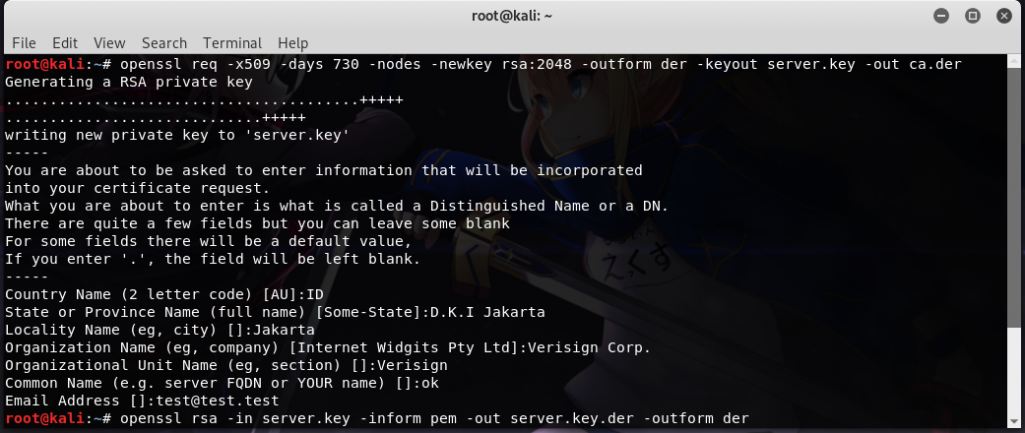
1.Set up your custom CA Certificate using OpenSSL 2.Import the generated CA certificate into the BurpSuite Proxy using the DER format This is what you will get […]
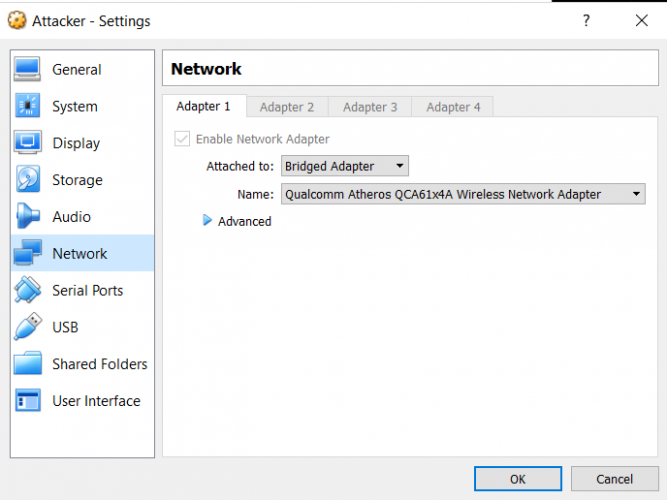
Change both machine’s network settings from “Attached to: NAT” to “Attached to: Bridged Adapter” Next, Get the victim machine’s IP address by running the ifconfig command on the command line […]